Why once a week backup is not enough
Backup is probably one of my favourite topics when it comes to data security. It’s relatively simple, it can save you from an unexpected disaster, it’s automated and in most cases, doesn’t require expensive or complicated setup.
Why backup?
If you own a car then you most likely have it insured because you never know what could happen due to your or someone else’s fault. You also probably have some form of health insurance in case you get sick or injured. Or not because you like living on the edge; I think you get the picture, insurance/backup is important and can save your butt without dipping into your hard-earned savings.
There are two kinds of people, “those who have had a storage failure and those who will have one in the future”.
3-2-1 strategy
What is 3-2-1 strategy you might ask? It means:
- Having 3 copies of your data
- On at least 2 different media
- And 1 being offsite
This concept has been popularised thanks to Peter Krogh, a well-known photographer who wrote that there are two kinds of people, “those who have had a storage failure and those who will have one in the future”.

3 – Having three copies of your data
Many people underestimate this requirement because they think one is enough. True, one is better than none but what if it’s the one that’s connected to your PC/Server that got fried during last night’s storm and took the backup drive to the silicon heaven with it? Your data would be gone. There are dozens of other reasons why you want to have three copies, such as viruses, ransomware, malicious damage, corruption and theft among others. It’s understandable that this setup isn’t always possible but there are tools that can help you with your most important documents, such as BackBlaze, CrashPlan or Carbonite. I’ll talk about cloud backup storage in my next blog.
2 – Data saved on at least two different media
You could have your data saved one a computer and a different partition but they could be physically still stored on the same hard-drive which would exposed them to the same risk as the main drive. Good effort but not the smartest. You can pick up an external drive from Staples, Officeworks or online for less than a $100 that would cover all your data. For businesses, there are paid and far better and more efficient tools based on very precise matrix. I won’t cover them here as this is more about generic, sound backup principles.
1 – Keep one copy offsite
Off-site copy is important in case something happens at the primary site, whether it’s loss, theft, fire or aforementioned lightning that can fry your data. Literally. For home, you can use solutions like CrachPlan, BackBlaze or Carbonite that will keep your data safe and in the cloud.
One note: don’t confuse backup tools with synchronisation tools (Dropbox, Google drive, Sync and so on), they are not the same thing! If you delete file on your hard-drive, it gets removed in your cloud storage immediately. True, you can often recover it within certain period of time but what if you don’t notice or forget or accidentally remove something you might need in the future, beyond the recovery period? It certainly happened to me. Luckily, I had a backup and was able to recover however my heartrate went up when I discovered that one of my contractors removed files from our shared folder because he was running out of space.
TLDR;
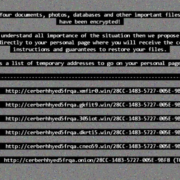
By now you understand the importance of backups and why you should keep one off-site or in the cloud. In case you’re still wondering and thinking ‘nah, it won’t happen to me!’, here’s a story from a client that had recently realised the importance of backups.
One of the employees received a social engineered email and curiously clicked on the link that loaded ransomware on their computer and started encrypting files on the computer as well as remote server. Most of their files got encrypted before they realised what had happened. They disconnected it and luckily we were able to disconnect the computer, clean it from pesky ransomware and restore the data on the server without much downtime. Not having functional backups would cause them headaches beyond ‘pay or not to pay’. If they had backup done only once a week, they would have to spend working overtime to catch up with all their work they did since the last backup. That’s why once a week backup isn’t the best idea – time is valuable and storage is dirt cheap. Talk to us today about free audit of your backup solutions.