The threat of ransomware has grown at an unprecedented rate, rising from being a menace to becoming by far the most common form of malware delivered to victims by cyberattackers.
In the space of a year, ransomware appears to have evolved on from the simple but effective strategy of locking down the files of infected targets until they pay a ransom, to incorporating additional malicious elements, such as stealing personal or financial data from the victim’s system.
While the success of ransomware demonstrates there are plenty of victims who’ll pay cybercriminals in order to get their files back, there are also schemes such as No More Ransom which allow them to restore their computer without having to part with a penny.
Now cybersecurity researchers warn that new ransomware features could make life even worse for victims. Rather than just encrypting key files, ransomware could soon infect a computer to such an extent that the only two options available to the user would be to pay, or to lose access to the entire system.
According to the Malwarebytes State of Malware Report 2017, we’re likely to see more variants of this type of ransomware, which is designed to modify the infected computer’s Master Boot Record, the part of the system which controls the ability to boot into the operating system.
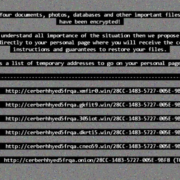
Once modified in this way using malicious code, the system will boot into a lock screen set up by the malware, demanding payment not only to decrypt files but also to restore access to the main operating system. The inability to do anything with the system aside from viewing the ransomware note will only give victims two options: pay up, or have their system wiped completely. It’s likely to make ransomware an even more appealing avenue of attack for cybercriminals.
Ransomware has boomed in the last year. The Malwarebytes report details how 12 months ago, ransomware was a threat to both individuals and organisations, accounting for almost one in five payloads delivered using exploits and spam emails.
Almost a year later, in November 2016, ransomware accounted for two thirds of all malicious payloads, making it by far the dominant form of malware, with the number of instances increasing by 267 percent. Ad fraud malware was a distant second place, accounting for one in ten malicious payloads.
Cybersecurity researchers catalogued nearly 400 variants of ransomware in the fourth quarter of last year alone, as cybercriminals across the globe attempted to cash in.
Unlike other forms of malware which often require the perpetrator to have some technical knowhow to deploy, the growth of ransomware-as-a-service has enabled even those without any coding skills to successfully hold victims’ data hostage until they receive a ransom payment — with a cut going to the ransomware developer.
While there are hundreds of variants of ransomware, three families dominated 2016: TeslaCrypt, Locky, and Cerber.
TeslaCrypt was the most dominant form of ransomware during the first half of 2016, before effectively being rendered useless by June, when its master decryption key was released.
Cerber and Locky quickly filled its place. Cerber became a particularly prevalent form of ransomware, because its as-a-service model means anyone can infect victims with it.
Meanwhile, Locky evolved to become the most notorious ransomware threat during 2016, even becoming the second most common malware threat by November. Despite a lull over Christmas, it shows no signs of slowing down, with instances of Locky once again on the up.
That’s bad news for the countries hit by the most ransomware attacks. The United States was the number one country to be targeted with ransomware attacks during 2016, followed Germany, Italy, the United Kingdom, and France.
The attacks against Western targets might not surprise. They are the countries with the most access to technology, and there’s also the potential that these states are being targeted for political reasons. The researchers points out that many cybercriminal syndicates work out of Eastern Europe.
“A country that seems to be missing from this list is Russia. This isn’t because Russian citizens have a firm grasp on computer security. Rather, it’s an indicator that Russian ransomware developers might shy away from targeting their own,” the report says.
Source www.zdnet.com