FBI: Reboot your router at home and business
Foreign cyber actors have been busy building another network of over 500k(!) IoT devices since 2012 to be ready for potential attack. Called VPNFilter, this malware attacks routers and NAS devices and awaits instructions from 2 domains. FBI had released a warning for users to restart their devices to remove the immediate threat of destroying their device. FBI also seized one of the URLs over the weekend and taken down the image from PhotoBucket were instructions were encoded.
Listening to your conversations? Possibly
“The VPNFilter malware is a multi-stage, modular platform with versatile capabilities to support both intelligence-collection and destructive cyber attack operations.”
Stage 1 persists through reboot and awaits deployment of stage 2. Stage 2 malware, which is not persistent after reboot, contains intelligence gathering capabilities, command execution, data exfiltration and device management.
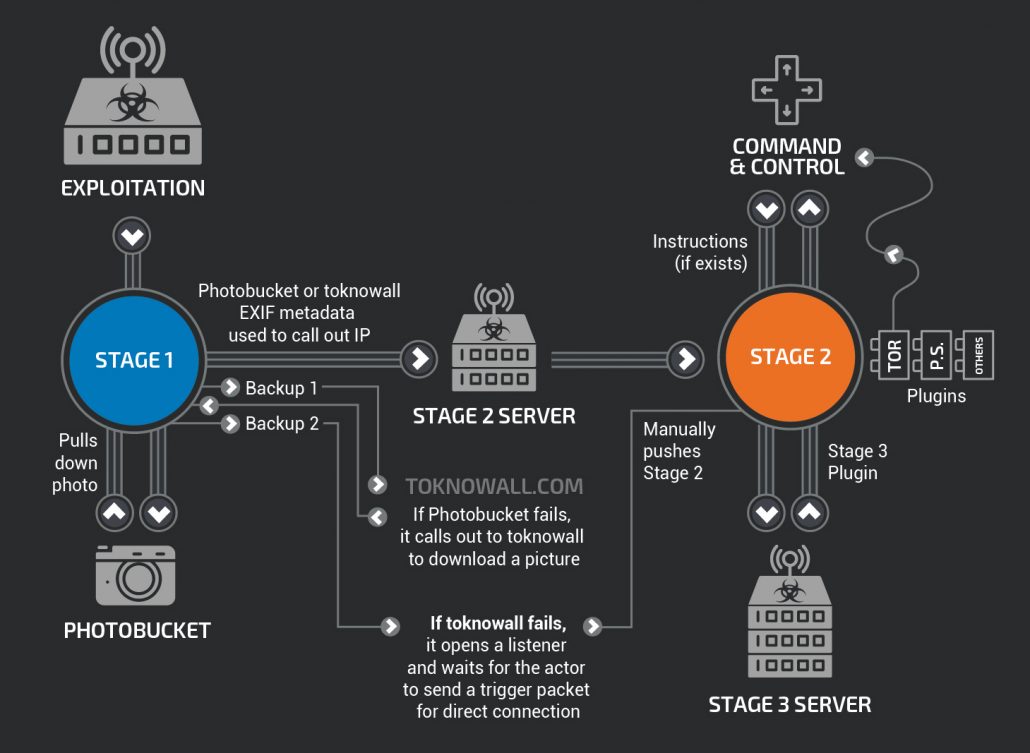
What to do?
If you have a router from the Linksys, MikroTik, NETGEAR and TP-Link or own a QNAP TS251 or TS439 Pro, do the following
- Restart your router/NAS
This will temporarily disable stage 2 and remove the immediate threat of bricking your device - Change your password to the device
As most device passwords are kept set as default, it will disable the direct access that was there before - Firmware update
Visit the manufacturer’s website or contact your ISP and install the latest firmware
More details can be found on the manufacturers websites
Source: Cisco Talos Intelligence




Leave a Reply
Want to join the discussion?Feel free to contribute!